What is SOC 2? The Ultimate Guide to SOC 2 Compliance & Certification
July 23, 2021 2021-10-01 10:19What is SOC 2? The Ultimate Guide to SOC 2 Compliance & Certification
What is SOC 2? The Ultimate Guide to SOC 2 Compliance & Certification
In this digital era, security and privacy is a must. Mishandling of sensitive data can leave companies vulnerable to attacks, such as data theft, extortion and malware installation.
To do good business, companies are increasingly being asked to provide a level of insurance around their information security programs. Therefore, Service Organization Control (SOC) reports are becoming more and more popular in data security and compliance, especially SOC 2.
But what is a SOC report? Do you need one? Which one do you need? Why is a SOC 2 report essential? Let’s dive in and see!
What is SOC 2?
What is a SOC 2 Report?
A SOC 2 report is a report that service organizations share with user organizations and stakeholders to demonstrate that a particular service is being provided securely, which is increasingly essential in today’s digital age.
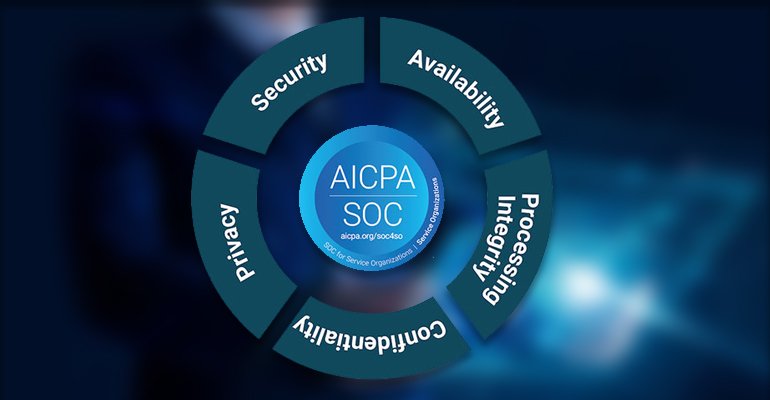
SOC 2 report/certification is issued by third-party auditors. They evaluate an organization’s information systems relevant to one or more of the five trust principles – security, availability, processing integrity, confidentiality, and privacy.
Audits are not conducted by the AICPA itself; instead, certified third-parties auditors are hired by vendors and service providers to get certified.
The SOC 2 audit is the auditor’s opinion on how that organization’s controls fit the requirements. The result of a clean (passed) opinion is that, according to the auditor, the data provider can be trusted as a secure service organization.
The two types of SOC 2 reports are:
- Type 1 describes the relevance of design controls and a description of a service provider’s approach.
- Type 2 focuses on the operational effectiveness of those systems.
The Five Trust Principles
The five trust principles are the core of SOC 2’s requirements, which must be reflected in the policies and procedures. The five Trust Services Criteria are:
Security: The system resources must be protected against unauthorized access (both physical and logical). Some IT security tools that ensure security are firewalls, 2FA (two-factor authentication) or MFA (multi-factor authentication), and intrusion detection.
Availability: A service organization must ensure that its information and systems are available and accessible so an organization can effectively function. It also reviews how often customers can access products and services. The availability criteria also demand that a company should have a documented business continuity and disaster recovery plan and procedures.
Processing integrity: Data and system processing must be accurate, complete, authorized and timely. Processing integrity is not included within SOC 2 as frequently as the availability and confidentiality of TSCs. Processing integrity is only relevant to companies that process transactions such as payments. This trust principle also details process monitoring and quality assurance.
Confidentiality: Confidential data—like business plans, IP content, and sensitive financial data—should remain protected and secure. Some practices for maintaining confidentiality are encryption, rigorous access controls, and network & application firewalls.
Privacy: The system’s collection, use, retention, disclosure and disposal of personal information should comply with the company’s data policies and AICPA’s Generally Accepted Privacy Principles (GAPP). 2FA, encryption, and proper access controls must be put in place to prevent unauthorized access.
Unlike other compliance regulations, companies need not cover all the five above. When you are audited, you will choose which trust principles you want to attest to. This is a business decision that depends on what is most important to your customers.
Who Needs a SOC 2 Report?
- Software as a service (SaaS) vendors.
- Companies that provide business intelligence and analytics services.
- Accounting and auditing businesses.
- IT security service providers.
- Pharmaceuticals.
- Legal firms.
- Managed Security Services (MSS) Providers.
- Insurance claims processing
- Human resources
- Data analysis
- Document and records management
- Workflow management
- Customer relationship management (CRM)
- Technology consulting.
How To Be a SOC 2 Compliant: 7 Simple Steps to Certification
Getting to SOC 2 compliance can be a tedious process, with a lot of moving parts, policies, and procedures to align. We suggest a methodical approach:
Step 1: Appoint your SOC 2 team members.
Step 2: Establish your goals. Do you want a Type 1 report or a Type 2 report? Do you want SOC 2 certification for a single product or service or your entire organization?
Step 3: Determine your scope. Begin by establishing which of the SOC 2 Trust Service Categories apply to your organization? Which of SOC 2’s 61 Trust Services Criteria (TSCs) apply to your company?
Step 4: Organize your materials. For each Trust Services Criterion, determine which controls apply. Evaluate whether they are effective, resolve any gaps, and gather the documents and correspondence proving the effectiveness of your controls. Organize evidence around the five trust categories: security, availability, confidentiality, processing integrity, and privacy of customer data.
Step 5: Self-audit. This step can save costs down the road. If the auditor finds any issues or gaps, it can drive up audit costs. However, thorough preparation using a SOC 2 audit checklist is your best bet here.
Step 6: Monitor yourself. Continuously monitoring for suspicious activities and setting up alarms to trigger when a security incident occurs can help keep you from falling out of compliance before the SOC 2 auditor arrives.
Step 7: Perform a SOC 2 audit. Call an independent Certified Public Accountant who is qualified to perform your SOC 2 audit. The audit process involves scoping, artefact document collection, and an on-site visit.
Get SOC 2 Compliance Preparations Started Today!
IRCLASS is here to help you.
We can help reduce the effort needed to gather required information while also helping you and your staff gain a deep understanding of the SOC 2 requirements.
To receive a quote, write to us at irqs.marketing@irclass.org. Get all your questions answered, choose the package that works best for you, and then you are ready to go!

