Category: Uncategorized

Demystifying ISO 27001: The Gold Standard for Information Security
The world has evolved, and operational systems have gone digital. The significance of information and data has grown exponentially. These are valuable assets for any company. Companies need to focus on the protection and security of the valuable data. Ensure optimal protection for the operational system and implement an adept information security management system or ISMS. It should be in accordance with the globally recognized standard ISO/IEC 27001. Having a concise overview of the critical aspects of ISO 27001 will help business owners identify the best techniques for ISMS development. Learn the essentialities and follow the best ways to ease the hassles. ISO 27001 is a global standard for information security management systems, and it is suitable for all companies regardless of the size. The global framework can facilitate the operations of a company and help them achieve the regulatory compliance objectives related to optimal data privacy and information security. ISO 27001 is an incredible tool to ensure assurance to customers, stakeholders, and business partners. Decoding ISO 27001 – A detailed overview ISO 27001 is a golden standard for the management of information security in companies. Why? Because it helps define the requirements behind successful documentation and implementation of a competent information security management system in the company. Currently, information security plays a noteworthy role for companies. And, ISO 27001 acts as an essential guide for both large and small companies. Both large corporations and small-scale startups can use the ISO standard, especially organizations operating in the tech sector. ISMS and ISO 27001 – The critical link ISMS, or information security management system, formulates the rules, techniques, and steps to ensure and continuously enhance information security at the company. It facilitates the availability, confidentiality, and integrity of data and information for employees, clients, suppliers, and shareholders. The system is relevant to small and large companies operating with sensitive data because the stakes for managing the security of the information are high. The practical need Cyber thefts are gradually increasing and necessitate media coverage. Thus, the significance and essentiality of covering these aspects has become paramount for companies. The extent of a cyber attack has also increased. It may not always be a large-scale public issue. The thefts can happen even on a “private” scale. In both cases, the effects could be devastating. ISO 27001 provides organizations with the essential guidelines for planning, implementing, controlling, and facilitating the information security. With strict protocols and optimal compliance, the confidentiality of critical data could be safeguarded. Also, ISMS ensures an enhancement of the entire IT infrastructure. The essentiality of ISO 27001 – Know them rightly 1. ISO 27001 enhances information security With ISO 27001, companies can structure their information security management. Vulnerabilities are easily identifiable with the ISO framework. One can detect them before they transform into security gaps. Additionally, it minimizes the adverse impact of hacker attacks, data loss, and misuse. Even if there is an attack, the companies can track and repair the issues efficiently. One can manage the risks and ensure better damage control with ISO 27001. 2. ISO 27001 improves confidence in information security A certified ISMS enhances credibility and trust. A company should be responsible enough to manage the critical data and information of the customers and business partners. A company can gain the trust of its partners and customers and ensure better data sharing. ISO 27001 is a renowned certification system. An efficient ISMS ensures optimal utilization and security of data. 3. ISO 27001 facilitates data transparency in the company ISO 27001 enhances the corporate infrastructure for cyber assets. Because, it involves all the departments to protect sensitive data. The framework defines management responsibility and promotes employee training. Information security could be seamlessly incorporated into the company’s operational schedule and routine, involving all employees. It creates a positive effect on business operations and improves data transparency. Benefits of ISO 27001 – Why is it the gold standard? Technical security measures like firewalls, antivirus, etc., are part of the ISMS checklists. But, these have a limited capacity to protect the information system. ISO 27001 delivers end-to-end solutions, defining the critical specification for an efficient information security management system. The certification defines the guidelines for data security and management. An ISMS delivers a holistic approach to cover critical aspects of information security, providing multi-tier protection solutions for clients, procedures, and technology. Protecting the assets with ISO 27001 One can protect hardware, software, processes, and other assets in a company with ISO 27001. It also helps maintain the asset register. One can maintain and monitor information assets, including everything related to business, operations, and personal data. Simply put, it is effective for everything that needs protection. It can also be financial data, sales data, HR data, etc. Summing note A well-defined and efficient ISMS makes an organization strong and helps a company minimize security risks. ISO framework is essential for ISMS establishment and its successful implementation. It is also vital for the operation, monitoring, and continual improvement of the ISMS, making the ISO 27001 standard an indispensable choice. With IRQS, find end-to-end solutions for audit services and ease the process. The experts bring efficient services with flawless audit reports for the best client experience.

8 Ways to Increase Your Business Cyber Security| Cyber security Guide
Cybersecurity is more important now than ever before. The threat of a data breach is always looming over your head. Hackers have become more sophisticated and they are now targeting small businesses with an intensity that was never before seen.

How to Apply for FSSAI Registration In India | Simple Step-by-Step Guide
If you want to run a food business legally in India, you first need an FSSAI registration.
Food Safety and Standards Authority of India (FSSAI), is a regulatory body in India that governs and oversees the food-related businesses specific to their quality and standards of the production process across the nation.
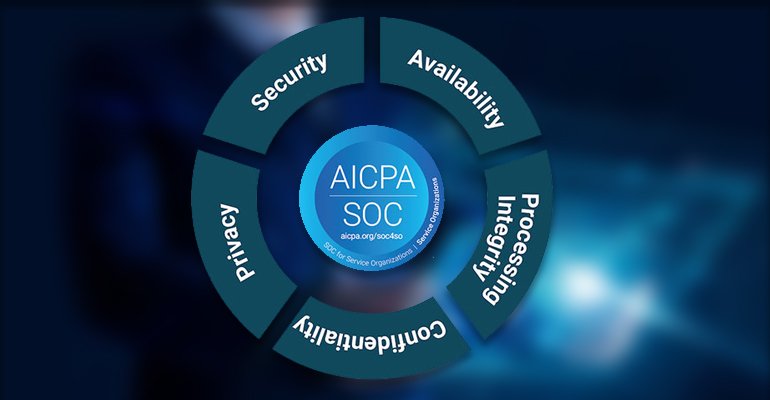
What is SOC 2? The Ultimate Guide to SOC 2 Compliance & Certification
In this digital era, security and privacy is a must. Mishandling of sensitive data can leave companies vulnerable to attacks, such as data theft, extortion and malware installation.
To do good business, companies are increasingly being asked to provide a level of insurance around their information security programs. Therefore, Service Organization Control (SOC) reports are becoming more and more popular in data security and compliance, especially SOC 2.

What Is ISO 27001? The Ultimate Guide To Certification
Information security breaches can be extremely dangerous to businesses both in terms of financial loss and reputational damage.
Implementing a robust security system can help mitigate the security risks, making the company more reliable and reputable in the eyes of potential customers, suppliers and business partners.

7 simple steps to Acquire An ISO 14001 Certification in India
So what’s all this buzz about ISO 14001 Certification and who needs it? There’s no simple answer to this. In short, this is an international standard that you’ll have to follow while designing and implementing EMS (Environmental Management System).

What is FSSC 22000 Certification & How it will Increase Your Revenue?
Irrespective of the tasty food products your business manufactures you need a robust food safety management system. Here’s why:
Without a firm food safety management system your food products could be susceptible to risks and threats which will affect both your consumers and your business.

Quality of Hand Sanitizers and Immunity booster products proven by “Ayush Mark Scheme”
Corona virus infection is spreading rapidly in recent times and proving to be to be a life threatening disease across the globe. The only way to combat this menace is by enhancing Personnel Hygiene and boosting immunity. Washing ones hand multiple times a day and intake of Immunity booster products would help to wage the war on the virus.
Search
Useful Links
Recent Posts
What Is Carbon Footprint Verification & Why It’s Critical for Your ESG Goals

Why ESG Reporting Is the Future of Business Strategy



